- padding-left:18px">
- traffic padding in network security
- Introduction To Traffic Padding In Network Security
- Purpose Of Traffic Padding In Deception And Masking
- CNSSI 4009-2015 As A Source Of Information On Traffic Padding
- Generating Fake Instances Of Communication And Data Units
- Concealing The Actual Amount Of Real Data Through Traffic Padding
- ISO/IEC 7498-2: The Standard Behind CNSSI 4009-2015
- Exploring The Concept And Technique Of Traffic Padding
- Creating Fake Instances Of Communication And Data Units
- Deceiving And Masking Through Traffic Padding
- Understanding CNSSI 4009-2015: The Standard On Traffic Padding
- FAQ
- What is the role of traffic padding in security mechanism?
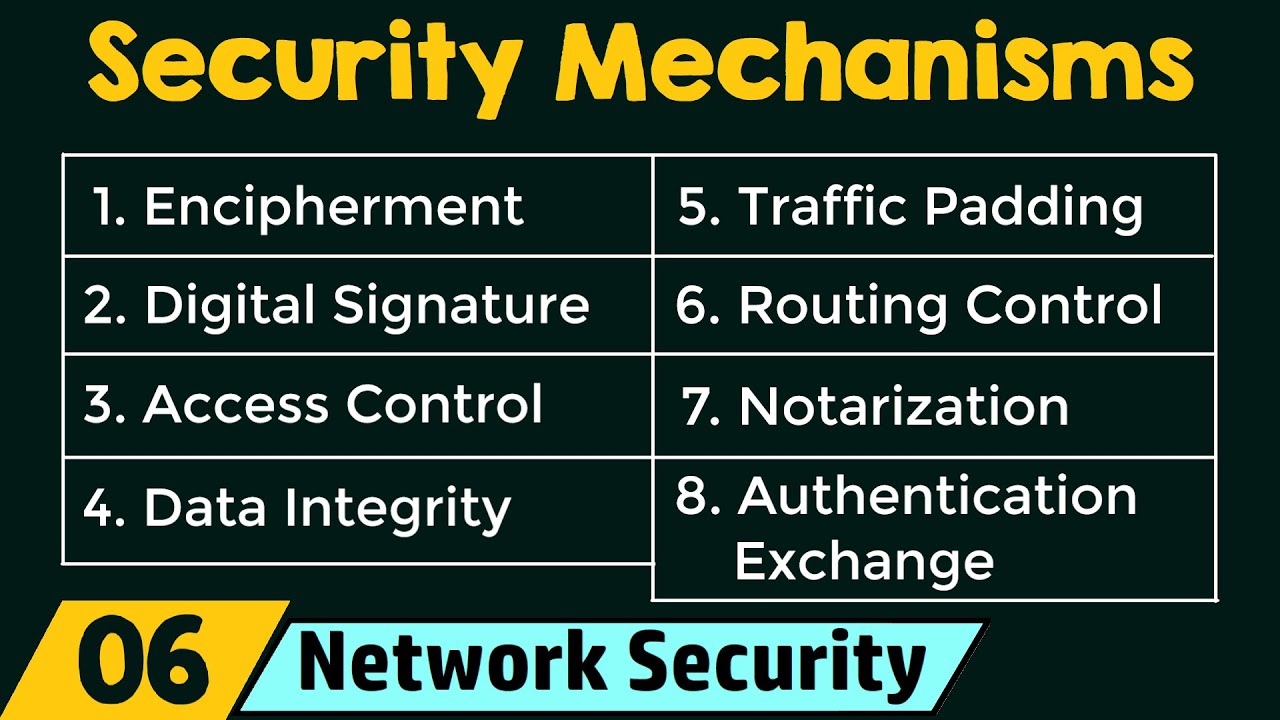
- What are the three security mechanisms?
- What is encipherment in network security?
- What is security padding?
In the ever-evolving landscape of networksecurity, a fascinating technique has emerged to cloak real data with a smokescreen of deception.
Enter traffic padding – a method that weaves intricate webs of fake communication and data units, warping the very fabric of digital communication.
Drawing insights from trusted sources like CNSSI 4009-2015 and ISO/IEC 7498-2, let us embark on a journey to unravel the intricate layers of this captivating technique.
| Item | Details |
|---|---|
| Topic | Exploring the Benefits and Implications of Traffic Padding: Enhance Network Security Efficiency |
| Category | Website Traffic |
| Key takeaway | In the ever-evolving landscape of network security, a fascinating technique has emerged to cloak real data with a smokescreen of deception. |
| Last updated | December 28, 2025 |
network-security">traffic padding in network security
Traffic padding in network security refers to the creation of fake instances of communication and data units within a network.
The purpose of traffic padding is to potentially deceive and mask the true amount of real data being sent.
It is a technique used to generate fake instances of communication and data units, often used to conceal the actual amount of real data being sent.
CNSSI 4009-2015, derived from ISO/IEC 7498-2, is a standard that provides information on traffic padding in network security.Key Points:
- Traffic padding in network security involves creating fake instances of communication and data units.
- The purpose of traffic padding is to potentially deceive and hide the true amount of real data being sent.
- It is a technique used to generate fake instances of communication and data units to conceal the actual amount of real data.
- CNSSI 4009-2015 is a standard that provides information on traffic padding in network security.
- The standard is derived from ISO/IEC 7498-2.
- Traffic padding is a measure to enhance network security.
Check this out:
? Did You Know?
1. Traffic padding in network security refers to the technique of adding random and irrelevant data to network traffic to confuse potential intruders. This method increases the difficulty of intercepting and deciphering sensitive information.
2. In ancient times, a form of traffic padding was used on the Silk Road to help protect valuable goods from theft. Caravans would intentionally include extra, less valuable items among their cargo to confuse potential robbers and throw them off the trail.
3. The concept of traffic padding in network security can be traced back to World War II, with the use of dummy radio transmissions to deceive enemy forces. These fake transmissions were designed to mimic real ones, thus obscuring communication signals and preventing the enemy from interpreting confidential messages.
4. A well-known example of traffic padding in network security is the use of “honey pots.” These are decoy systems that appear vulnerable to attackers but are actually closely monitored by security professionals. By attracting hackers and studying their behaviors, organizations can strengthen their defenses and stay one step ahead of potential threats.
5. Traffic padding can be used to counter timing-based attacks in network security. By adding unpredictable delays in network traffic, it becomes much harder for attackers to precisely time their actions, decreasing the likelihood of successful attacks on sensitive information.
Introduction To Traffic Padding In Network Security
In the realm of network security, traffic padding has gained recognition as a technique used to enhance security measures and protect the privacy and integrity of transmitted information. This concept involves the creation of fake instances of communication and data units within a network to potentially deceive and mask the true amount of real data being sent.
By employing traffic padding, network administrators can:
- Enhance security measures
- Maintain privacy of transmitted information
- Ensure the integrity of data being sent
Using this approach, network administrators can effectively protect against unauthorized access and malicious attacks.
“Traffic padding is a powerful technique in network security that involves the creation of fake instances of communication and data, helping to deceive and mask the true amount of real data being sent.”
Purpose Of Traffic Padding In Deception And Masking
The primary purpose behind the use of traffic padding is to deceive and mask the actual amount of real data being sent across a network. By generating additional fake instances of communication and data units, it becomes difficult for unauthorized individuals or adversaries to determine the true extent of legitimate information being transmitted. This technique enhances security by obscuring the patterns and sizes of real data, making it more challenging for malicious actors to gain insights into sensitive network activities.
CNSSI 4009-2015 As A Source Of Information On Traffic Padding
For those seeking information regarding traffic padding in network security, CNSSI 4009-2015 serves as a valuable resource. This document provides in-depth insights into the technique of traffic padding, offering guidance and recommendations on its implementation for improved security. Derived from the ISO/IEC 7498-2 standard, CNSSI 4009-2015 ensures that individuals and organizations have access to a comprehensive reference for understanding traffic padding and its implications in network security.
Generating Fake Instances Of Communication And Data Units
One of the fundamental aspects of traffic padding is the generation of fake instances of communication and data units. Through this technique, network administrators can introduce simulated traffic to the network that mirrors the behavior of real communication. By creating these fabricated instances, the true amount of real data being transmitted becomes obfuscated, thereby enhancing security measures by posing a challenge to potential eavesdroppers or attackers.
Concealing The Actual Amount Of Real Data Through Traffic Padding
By utilizing traffic padding, network administrators can effectively conceal the actual amount of real data being transmitted across the network. This technique ensures that the quantity and size of true information are obscured by the presence of additional fake instances and data units. As a result, unauthorized individuals are unable to discern the actual volume of sensitive data being transmitted, enhancing overall network security.
Benefits of traffic padding:
- Conceals the actual volume of sensitive data
- Enhances network security
This post updated with new ad network performance data.
“By utilizing traffic padding, network administrators can effectively conceal the actual amount of real data being transmitted across the network.”
ISO/IEC 7498-2: The Standard Behind CNSSI 4009-2015
ISO/IEC 7498-2 serves as the foundation for CNSSI 4009-2015, the standard from which information on traffic padding is derived. This international standard specifically focuses on the structure and operation of network security systems. ISO/IEC 7498-2 provides a comprehensive framework for the establishment of network security policies and protocols, including the implementation of techniques like traffic padding.
Exploring The Concept And Technique Of Traffic Padding
The concept and technique of traffic padding in network security are intriguing avenues to explore. By generating fake instances of communication and data units, network administrators can manipulate network traffic to enhance security measures. This technique ensures that the true amount of real data remains hidden, thus deterring potential attacks and unauthorized access.
Creating Fake Instances Of Communication And Data Units
To enhance network security, network administrators can employ traffic padding by generating counterfeit instances of communication and data units. These fabricated instances are designed to imitate real communication patterns, tricking potential adversaries or eavesdroppers. By incorporating these simulated instances into the network, the true volume of actual data is obscured, effectively bolstering network security.
Deceiving And Masking Through Traffic Padding
The key objective of traffic padding is to deceive and mask the true amount of real data being transmitted across a network. By employing this technique, network administrators aim to mislead potential attackers and eavesdroppers by generating additional fake instances of communication and data units. This deceptive tactic adds a layer of protection to the network, making it challenging for unauthorized individuals to interpret genuine network activities accurately.
Understanding CNSSI 4009-2015: The Standard On Traffic Padding
For a comprehensive understanding of traffic padding in network security, CNSSI 4009-2015 is a crucial standard to reference. Derived from ISO/IEC 7498-2, this document provides a wealth of information on traffic padding, including its theory, implementation, and best practices. Network administrators and security professionals can leverage this standard to enhance their knowledge and proficiency in traffic padding for improved network security.
FAQ
What is the role of traffic padding in security mechanism?
Traffic padding plays a critical role in security mechanisms by thwarting traffic analysis attempts. By inserting additional bits into gaps in an information flow, traffic padding creates artificial traffic patterns that make it challenging for attackers to discern patterns and extract meaningful information from the data. This technique strengthens the confidentiality and integrity of communication channels by adding a layer of obfuscation, making it more difficult for potential adversaries to identify and exploit vulnerabilities in the system. By counteracting traffic analysis attempts, traffic padding enhances the overall security posture and ensures the privacy of sensitive information in transit.
What are the three security mechanisms?
In addition to the widely-used security mechanisms of Secure Socket Layer (SSL) Encryption, authentication and firewalls serve as vital components in safeguarding sensitive data and protecting against unauthorized access. SSL Encryption is a cryptographic protocol that ensures secure communication between a client and a server, preventing eavesdropping and tampering of data during transmission. Authentication, on the other hand, involves verifying the identity of individuals or systems attempting to access a network or a resource. By requiring users to provide valid credentials, such as usernames and passwords, authentication helps ensure that only authorized individuals are granted access. Lastly, firewalls act as a protective barrier between networks, meticulously monitoring incoming and outgoing traffic to prevent potential threats and malicious activities from infiltrating protected systems.
What is encipherment in network security?
Encipherment in network security is a critical technique used to ensure the confidentiality of data. By employing mathematical calculations or algorithms, encipherment transforms information into an unreadable format, thereby preventing unauthorized access and protecting sensitive data. Through this process, data is encrypted to such an extent that it becomes extremely difficult for potential attackers to decipher and comprehend, thus enhancing the security of networks and information systems.
What is security padding?
Security padding refers to the practice of adding additional characters or bytes to a message, particularly in the context of classical ciphers. Its main purpose is to hinder cryptanalysts from exploiting predictability within the encryption and identifying known plaintext, which would facilitate breaking the encryption. By introducing random length padding, it also prevents attackers from determining the precise length of the original message, further enhancing security. Overall, security padding acts as a proactive measure to limit the vulnerabilities that could be exploited by adversaries during the encryption process.
Advertising Platform for Marketers • Self-Serve DSP Platform • Performance Marketing Tips • Buy Traffic • Programmatic Advertising