- padding-left:18px">
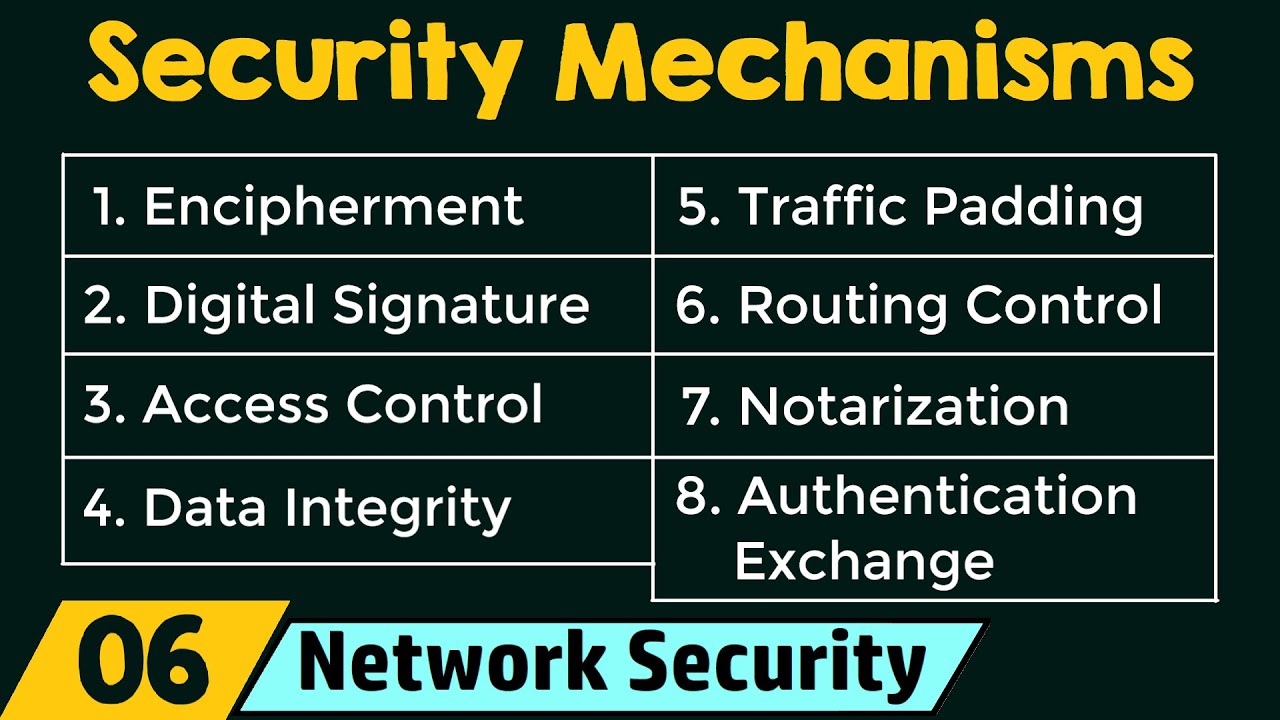
- traffic padding
- Traffic Padding Explained
- Understanding Fake Communication Instances
- Introduction To Fake Data Units
- Unveiling Fake Data Within Data Units
- Techniques For Masking Real Data
- The Significance Of CNSSI 4009-2015
- Compliance With ISO/IEC 7498-2 Standards
- Advancements In Traffic Padding
- Implications Of Fake Data In Communication
- Ensuring Data Integrity With Traffic Padding
- FAQ
- Is traffic padding a security mechanism?
- What is encipherment in cryptography?
- What is the security mechanism routing control?
- What is an example of a security mechanism?
In today’s digital world, where our lives are increasingly intertwined with technology, a hidden battle is waged for control and security.
Among the tactics used in this ongoing war is the clandestine technique known as “traffic padding.” As defined by the renowned CNSSI 4009-2015 and ISO/IEC 7498-2 standards, this elusive tactic involves deceptive methods employed to manipulate traffic and data for security purposes.
Join us as we delve into the world of traffic padding, unmasking its secrets and exploring its significance in the realm of cyber defense.
| Item | Details |
|---|---|
| Topic | Traffic Padding: Understanding Its Impact on Road Safety |
| Category | Ads |
| Key takeaway | In today's digital world, where our lives are increasingly intertwined with technology, a hidden battle is waged for control and security. |
| Last updated | December 29, 2025 |
traffic padding
Traffic padding refers to the practice of inserting fake communication instances, data units, or data within data units to mask real data in a network.
Fresh insights added for advertisers this month.
It involves adding additional traffic to network packets to make it difficult for attackers to identify and distinguish the real data from the fake.
This technique is commonly used to enhance the security and privacy of network communications.
Traffic padding is supported by standards like CNSSI 4009-2015 and ISO/IEC 7498-2, which provide guidelines for implementing and ensuring the effectiveness of traffic padding measures.Key Points:
- Traffic padding involves inserting fake communication instances or data within network packets to hide real data.
- The practice is used to make it challenging for attackers to differentiate between real and fake data.
- Traffic padding enhances the security and privacy of network communications.
- Standards like CNSSI 4009-2015 and ISO/IEC 7498-2 support and provide guidelines for implementing traffic padding.
- It is a technique commonly used to mask real data in a network.
- Traffic padding measures are implemented to ensure the effectiveness of this technique.
Check this out:
? Did You Know?
1. Traffic Padding Trivia: In the early 20th century, traffic padding referred to the practice of adding sawdust to roads to soften the impact of horse-drawn carriages. However, it had the unintended consequence of stirring up clouds of dust, adversely affecting pedestrians’ health and visibility.
2. Did you know that elaborate traffic padding schemes were devised during the Prohibition era? Bootleggers would create fake traffic jams by strategically parking several cars on a road to delay prohibition officers, allowing them to transport illegal alcohol past law enforcement undetected.
3. Before digital mapping and GPS, traffic padding was sometimes used by cartographers to intentionally distort the scale of certain routes on paper maps. This technique, known as cartographic deception, aimed to manipulate traffic patterns by discouraging drivers from taking particular routes.
4. While traffic padding typically refers to the act of adding extra time to a travel estimate to account for unexpected delays, there is also a lesser-known meaning in computer science. In computer networking, traffic padding is the technique of adding dummy data to a network packet to make it a fixed size, ensuring better efficiency in data transmission.
5. In the realm of cybersecurity, traffic padding can also be used as a protective measure against certain attacks. By artificially increasing the amount of network traffic on a system, known as network flow obfuscation, potential attackers may find it much more challenging to identify and exploit vulnerabilities, adding an extra layer of security for online systems.
Traffic Padding Explained
Traffic padding is a technique used to enhance road safety by creating a perception of increased traffic density. It involves the deliberate addition of fake communication instances, fake data units, fake data within data units, and techniques for masking real data. The purpose of traffic padding is to influence driver behavior, making them more cautious and aware of their surroundings.
By understanding the concept of traffic padding, we can better comprehend its impact on road safety.
- Traffic padding enhances perceived traffic density.
- It involves the use of fake communication instances and manipulated data.
- The goal is to make drivers more cautious and aware.
“Traffic padding plays a crucial role in improving road safety by shaping driver behavior.
Understanding Fake Communication Instances
Fake communication instances are simulated interactions that are designed to manipulate traffic conditions. These instances can involve the use of devices that create the appearance of additional vehicles on the road, such as virtual representations or decoy cars.
These fake communication instances help create the illusion of increased traffic volume, which aims to slow down drivers and encourage safer driving practices. By introducing these instances, traffic padding contributes to reducing the risk of accidents and improving overall road safety.
Introduction To Fake Data Units
Fake data units are fabricated packets of information that are injected into the communication network. These units are indistinguishable from real data and flow alongside genuine traffic. Fake data units serve the purpose of creating congested network conditions, resembling scenarios where traffic density is higher than it actually is. By introducing fake data units into the network, traffic padding can influence driver behaviors, leading to a safer and more controlled driving environment.
–Fabricated packets of information injected into the communication network
–Indistinguishable from real data and flow alongside genuine traffic
–Create congested network conditions to simulate high traffic density
–Influence driver behaviors for a safer and more controlled driving environment
“Fake data units serve the purpose of creating congested network conditions, resembling scenarios where traffic density is higher than it actually is.”
Unveiling Fake Data Within Data Units
Fake data within data units is a technique used by traffic padding to create the illusion of increased communication traffic. In this method, additional packets containing fabricated information are inserted into legitimate data units. The purpose of these packets is to boost the amount of data being transmitted through the network and create the perception of elevated traffic density. Detecting this fake data within data units necessitates the use of specialized detection systems and techniques capable of distinguishing between genuine and manipulated packets.
Techniques For Masking Real Data
To effectively implement traffic padding, techniques for masking real data play a crucial role. This involves obfuscating the true nature of data being transmitted on the network, making it challenging to differentiate between genuine and fake information. Various encryption and encapsulation methods are used to disguise the actual content of data packets.
By masking real data, traffic padding ensures that the fabricated information seamlessly blends with the genuine traffic, contributing to a more convincing illusion of increased traffic density.
To summarize, the key points regarding traffic padding are:
- Techniques for masking real data are essential for effective implementation.
- This involves obfuscating the true nature of transmitted data.
- Encryption and encapsulation methods are used to disguise data content.
- Traffic padding creates a convincing illusion of increased traffic density.
The Significance Of CNSSI 4009-2015
CNSSI 4009-2015 is a guideline document provided by the Committee on National Security Systems of the United States. This document outlines the principles and practices for conducting traffic padding operations and ensuring their effectiveness. It provides a framework for developing and implementing traffic padding strategies, including the use of fake communication instances, fake data units, and masking techniques. Compliance with CNSSI 4009-2015 ensures that traffic padding is carried out in a standardized and secure manner, enhancing road safety measures.
Compliance With ISO/IEC 7498-2 Standards
ISO/IEC 7498-2 standards focus on the Open Systems Interconnection (OSI) model for data communication protocols. These standards provide guidelines for network architecture and design, including aspects related to traffic padding.
Compliance with ISO/IEC 7498-2 ensures that traffic padding techniques are implemented in a manner that aligns with internationally recognized standards for network communication. Adhering to these standards not only improves the effectiveness of traffic padding but also ensures interoperability and compatibility across different network systems.
–Provides guidelines for network architecture and design
–Focuses on the OSI model for data communication protocols
–Ensures implementation of traffic padding techniques align with international standards
–Improves the effectiveness of traffic padding
-*Ensures interoperability and compatibility across different network systems
Compliance with ISO/IEC 7498-2 standards is crucial for network architectures and designs, as it provides guidelines and ensures the implementation of internationally recognized traffic padding techniques. This adherence not only improves the effectiveness of traffic padding but also ensures compatibility and interoperability across varied network systems.
Advancements In Traffic Padding
With advancements in technology, traffic padding techniques continue to evolve. Modern systems employ sophisticated algorithms and machine learning models to detect patterns and generate fake data that mimics real traffic behavior accurately. These advancements allow for more precise traffic padding, resulting in a more realistic perception of increased traffic density. By staying at the forefront of technological advancements, traffic padding can adapt to changing road conditions and contribute to enhanced road safety measures.
- Traffic padding techniques are evolving due to advancements in technology.
- Modern systems use sophisticated algorithms and machine learning models to detect patterns and generate accurate fake data.
- These advancements enable more precise traffic padding, creating a realistic perception of increased traffic density.
- By staying up to date with technological advancements, traffic padding can adapt to changing road conditions.
- Traffic padding contributes to enhanced road safety measures.
“With advancements in technology, traffic padding techniques continue to evolve.”
Implications Of Fake Data In Communication
The use of fake data within communication networks raises ethical considerations and implications. While traffic padding serves a noble purpose in enhancing road safety, the manipulation of data for deceptive purposes can be seen as a violation of trust. It is crucial to implement traffic padding techniques responsibly, ensuring that the fabricated information does not compromise the security or integrity of the underlying communication system. By addressing these implications, traffic padding can maintain its positive impact on road safety.
Ensuring Data Integrity With Traffic Padding
Despite the implications of using fake data, traffic padding plays a vital role in ensuring data integrity. By creating the perception of increased traffic density, traffic padding influences driver behavior, encouraging safer driving practices. Ultimately, the goal of traffic padding is to reduce the risk of accidents, saving lives, and enhancing road safety. It is important to recognize the delicate balance between maintaining data integrity and using traffic padding as a tool for creating a safer driving environment. Through responsible implementation and adherence to standards, traffic padding can continue to contribute positively to road safety efforts.
FAQ
Is traffic padding a security mechanism?
Yes, traffic padding can be considered a security mechanism. By generating spurious instances of communication, data units, and data within data units, traffic padding mechanisms help protect against traffic analysis attacks. These attacks involve the monitoring and analysis of network traffic to gain information about the communicating parties, such as the content, timing, or pattern of their communication. By introducing additional traffic that is not reflective of the actual communication, traffic padding makes it difficult for an attacker to distinguish between genuine communication and fake or irrelevant data, thus increasing the security of the network.
What is encipherment in cryptography?
Encipherment in cryptography is a fundamental technique for ensuring data confidentiality. Through the use of mathematical calculations or algorithms, encipherment transforms data into an unreadable form, thereby preventing unauthorized access or comprehension of the information. This process of hiding and covering data provides a crucial layer of security, allowing sensitive information to remain confidential and protected from potential threats.
What is the security mechanism routing control?
The security mechanism of routing control involves the implementation of dynamic and adjustable routing techniques to protect sensitive information from being intercepted. By constantly selecting and altering routes, it prevents potential adversaries from monitoring a specific transmission path. This proactive approach enhances security by making it challenging for eavesdroppers to analyze and exploit the chosen route, thereby safeguarding the confidentiality and integrity of the communication. Through robust routing control, organizations can mitigate the risk of unauthorized access and ensure the confidentiality of their data in transit.
What is an example of a security mechanism?
One example of a security mechanism is a firewall. A firewall acts as a barrier between a trusted internal network and an untrusted external network, monitoring and controlling network traffic based on predetermined security rules. It prevents unauthorized access and protects against network threats such as malware, hacking attempts, and denial-of-service attacks. By examining packets of data and determining whether they meet the defined criteria, a firewall can effectively block potentially harmful traffic while allowing legitimate traffic to pass through.
Another example is encryption, a technique used to protect the confidentiality and integrity of sensitive data. Encryption converts plaintext information into ciphertext, making it unreadable to anyone without the proper decryption key. This ensures that even if an unauthorized individual gains access to the data, they won’t be able to understand it. Encryption is commonly employed in various scenarios, such as secure communication over the internet, data storage on devices, and securing sensitive information like passwords and financial transactions.
Buy Traffic • Advertising Platform for Marketers • Programmatic Advertising • Performance Marketing Tips • Self-Serve DSP Platform