- advertisement pop up virus
- Introduction To Adware: A Sneaky Type Of Malware
- How Adware Infects Devices: Tricky Techniques And Hidden Downloads
- The Effects Of Adware: Unwanted Ads, Pop-Ups, And Redirects
- Understanding Adware Vs. Legitimate Software Applications
- Adware And Personalized Ads: Analyzing Behavior For Targeted Advertising
- The Potential Threat Of Adware: User Data Sold To Third Parties
- Adware’s Impact On Browsers: Chrome, Firefox, And More
- Signs Of Adware Infection: Unexpected Ads And Browser Changes
- The Rise Of Adware: Increased Volume And New Techniques
- Protecting Against Adware: Removal Techniques And Prevention Measures
- FAQ
- 1. How can users protect their devices from advertisement pop-up viruses?
- 2. What are the common signs and symptoms of an advertisement pop-up virus infecting your device?
- 3. What are the potential risks and consequences of clicking on or interacting with advertisement pop-up viruses?
- 4. How do advertisement pop-up viruses manage to bypass antivirus software and infect devices?
Do you ever feel like your computer is haunted by pesky ads that seem to pop up out of nowhere?
Well, you’re not alone.
Adware, the notorious ghost of the cyber world, has been causing chaos and frustration to millions of users worldwide.
This sneaky malware lurks in the shadows, displaying unwanted ads and even spying on your online activities.
But fear not!
In this article, we’ll unveil the secrets to banishing this adware ghost for good, with the help of powerful cybersecurity tools like Malwarebytes.
Get ready to take back control of your digital realm!
| Item | Details |
|---|---|
| Topic | Advertisement Pop Up Virus: Protect Yourself from Cyber Threats |
| Category | Marketing |
| Key takeaway | Do you ever feel like your computer is haunted by pesky ads that seem to pop up out of nowhere? Well, you're not alone. |
| Last updated | December 29, 2025 |
pop-up-virus">advertisement pop up virus
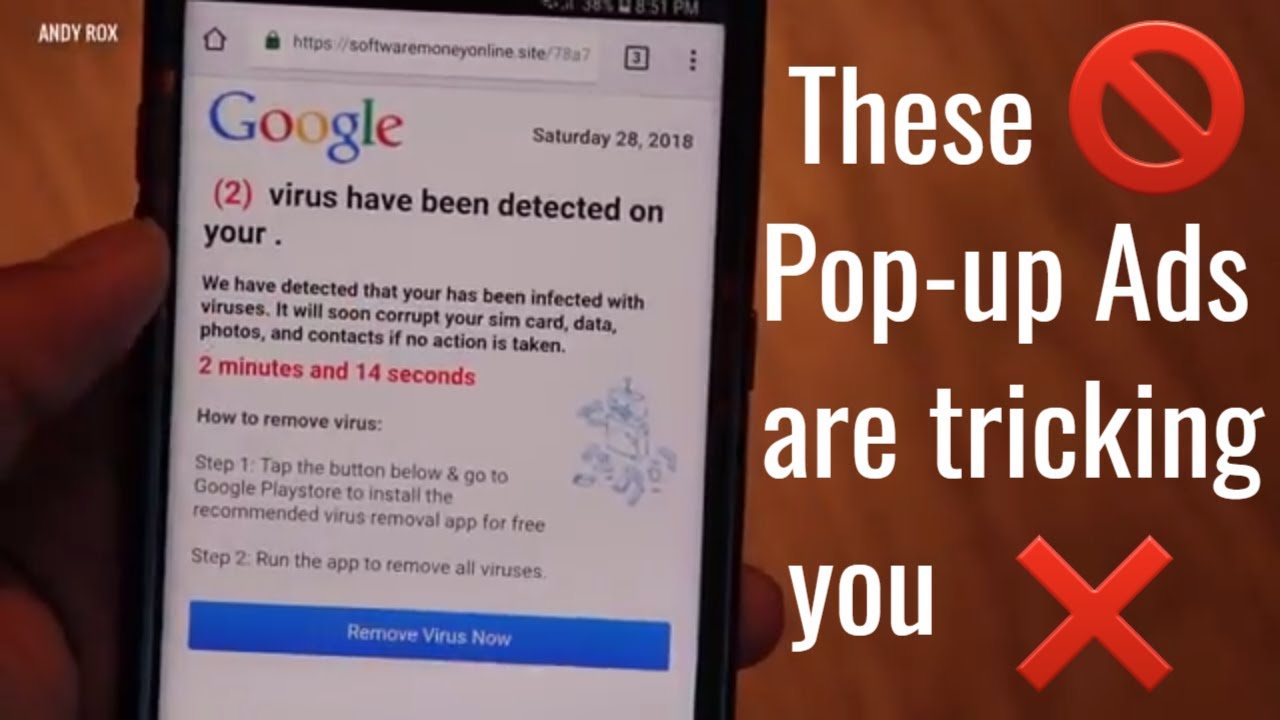
The term “advertisement pop up virus” refers to adware, which is a type of malicious software that installs itself on devices and displays unwanted advertisements and pop-ups.
Adware can track online behavior and display personalized ads, and it often disguises itself as legitimate software or piggybacks on another program to trick users into installing it.
While adware is more of a nuisance than a harmful malware threat, it can cause new tabs to open, change the home page, redirect to unfamiliar search engines, and display dubious ads.
It affects all browsers, including Chrome and Firefox, and can be unknowingly downloaded when users download freeware or shareware programs or visit infected websites.
To remove adware, it is suggested to use the utility on the operating system or a legitimate cybersecurity program.
It is important to exercise caution when downloading and installing new software and to regularly scan and update cybersecurity tools to prevent adware infections.Key Points:
- “Advertisement pop up virus” refers to adware, a type of malicious software that displays unwanted advertisements and pop-ups.
- Adware can track online behavior, display personalized ads, and often disguises itself as legitimate software.
- Adware can cause new tabs to open, change the home page, redirect to unfamiliar search engines, and display dubious ads.
- It affects all browsers, including Chrome and Firefox, and can be unknowingly downloaded when users download freeware or visit infected websites.
- To remove adware, it is suggested to use the utility on the operating system or a legitimate cybersecurity program.
- It is important to exercise caution when downloading and installing new software and regularly scan and update cybersecurity tools to prevent adware infections.
Check this out:
? Did You Know?
1. One advertising pop-up virus named “CoolWebSearch” was notorious for redirecting users to malicious websites. It earned an estimated $2 million per year for its creators by generating fake clicks and traffic.
2. The term “malvertising” refers to the malicious use of online advertising to spread viruses or malware. Advertisements can contain hidden code that infects a user’s computer when clicked, making it important to stay cautious while browsing the web.
3. Advertisements related to healthcare are more likely to contain malicious code. Cybercriminals exploit people’s desire for health-related information, making healthcare-related pop-up ads a breeding ground for virus distribution.
4. Advertisements on mobile devices can sometimes route users to fake App Store pages that look legitimate. These spoofed pages prompt users to download malicious apps, compromising their devices and personal information.
5. Some advertisers use “clickjacking” techniques to trick users into unintentionally clicking on ads. By overlaying the ad with invisible elements or by disguising it as a different object, users can be led to unintended destinations, including virus-infected webpages.
Introduction To Adware: A Sneaky Type Of Malware
Adware, short for advertising-supported software, is a malicious form of software that infiltrates devices and bombards users with unwanted advertisements and pop-ups. It is classified as malware due to its unconsented installation and disruptive intrusive ads. Adware is typically bundled with legitimate software or disguised as a legitimate program, deceiving users into unknowingly installing it on their devices.
- Adware is a form of malicious software that displays intrusive ads.
- It installs itself without the user’s consent.
- Adware is often bundled with legitimate software or disguised as a legitimate program.
How Adware Infects Devices: Tricky Techniques And Hidden Downloads
Adware employs deceptive techniques to infect devices and gain access to users’ browsers. One common method is through the download of freeware or shareware programs, where adware piggybacks on the installation process unnoticed. By disguising itself as a harmless program, adware sneaks its way onto the user’s device without raising suspicion.
Additionally, adware can exploit vulnerabilities in web browsers, infecting websites and initiating a drive-by download. This means that users can inadvertently download adware simply by visiting an infected website. These hidden downloads are especially dangerous as they bypass the user’s consent and infect the device without their knowledge.
- Adware employs deceptive techniques to infect devices and gain access to users’ browsers.
- Adware piggybacks on the installation process of freeware or shareware programs.
- Adware disguises itself as a harmless program to avoid suspicion.
- Adware can exploit vulnerabilities in web browsers to initiate a drive-by download.
- Users can unknowingly download adware by visiting an infected website.
- Hidden downloads bypass the user’s consent and infect the device without their knowledge.
The Effects Of Adware: Unwanted Ads, Pop-Ups, And Redirects
Once adware has successfully infiltrated a device, it starts to manifest its presence through various annoying and disruptive behaviors. Users may start seeing an influx of unwanted ads and pop-ups appear on their screens, even when they are not actively browsing the internet. These ads can range from dubious weight loss programs to get-rich-quick offers and fake virus warnings, all designed to prey on unsuspecting users.
In addition to intrusive ads, adware can also manipulate the user’s browser settings. It may open new tabs, change the homepage, redirect searches to unfamiliar search engines, or even lead to NSFW (Not Safe for Work) websites. These changes can be frustrating, as they alter the user’s browsing experience and can be quite difficult to undo without the proper knowledge and tools.
- Unwanted ads and pop-ups can appear even when not actively browsing
- Ads range from weight loss programs to get-rich-quick offers and fake virus warnings
- Adware manipulates browser settings: opening new tabs, changing homepage, redirecting searches
- Can lead to NSFW websites
- Changes are frustrating and difficult to undo without proper knowledge and tools
Understanding Adware Vs. Legitimate Software Applications
While legitimate software applications also use online advertising to generate revenue, adware is fundamentally different. Legitimate software typically displays advertisements within the boundaries of the program itself, respecting the user’s consent and providing relevant and non-intrusive ads.
Adware, on the other hand, goes against the user’s will, flooding their screens with unwanted ads and disrupting their online activities.
It is essential to distinguish between legitimate software applications and adware to avoid falling victim to the latter. Understanding the differences helps users make informed decisions when downloading or installing new software on their devices.
To summarize, the key differences between legitimate software and adware are:
- Legitimate software displays advertisements within the program’s boundaries.
- Legitimate software respects user consent.
- Legitimate software provides relevant and non-intrusive ads.
- Adware goes against the user’s will.
- Adware floods screens with unwanted ads.
- Adware disrupts online activities.
As a reminder, users should be cautious when downloading or installing new software and ensure that it comes from a reliable source to avoid unintentionally installing adware.
Adware And Personalized Ads: Analyzing Behavior For Targeted Advertising
One of the defining characteristics of adware is its ability to track users’ online behavior and display personalized advertisements. Adware can analyze a user’s location, browsing history, and website visits to provide targeted advertisements that are seemingly relevant to their interests.
While adware may not be as harmful as other forms of malware, the invasive nature of personalized ads raises concerns about user privacy. The browsing behavior and information collected by adware can be sold to third parties, who then use this data to create further targeted advertising campaigns.
The Potential Threat Of Adware: User Data Sold To Third Parties
Although adware itself is not highly threatening to users’ devices, the data it collect is definitely a cause for concern. The information that adware gathers, such as browsing habits and preferences, can be sold to third parties for targeted advertising purposes, which can invade users’ privacy. This raises huge privacy issues, as many users might not even know that their personal data is being shared without their consent.
To ensure their personal data is safe, it is crucial for users to be cautious and vigilant when downloading software, particularly programs that display advertisements. Carefully reading the terms and conditions, as well as thoroughly understanding the privacy policies of software applications, can help users protect their personal information from being exploited by adware developers.
Adware’s Impact On Browsers: Chrome, Firefox, And More
Adware can affect all browsers, including popular ones like Google Chrome and Mozilla Firefox. Regardless of the browser used, adware has the ability to manipulate browser settings and disrupt the user’s online experience.
When browsing the internet, users might encounter unexpected advertisements in various places on the webpage. These ads can be intrusive and may even hinder the user’s ability to navigate the website.
Additionally, adware can modify the browser’s homepage, leading to unwanted search engines or redirecting the user to unfamiliar websites.
The widespread impact of adware on various browsers highlights the importance of staying vigilant and taking precautions to protect against this type of malware.
n- Adware affects all browsers, including popular ones like Google Chrome and Mozilla Firefox.
n- Adware can manipulate browser settings and disrupt the user’s online experience.
n- Users might encounter unexpected advertisements on webpages.
n- These ads can be intrusive and hinder the user’s ability to navigate.
n- Adware can modify the browser’s homepage, leading to unwanted search engines or unfamiliar websites.
n- Stay vigilant and take precautions to protect against adware.
Signs Of Adware Infection: Unexpected Ads And Browser Changes
Detecting the presence of adware on a device is crucial in order to take suitable action to remove it. There are certain signs that indicate a potential adware infection.
One of the most noticeable signs is the sudden appearance of ads in unexpected places, both within and outside of the user’s browser.
Another sign of adware infection is when the user’s browser settings change without their consent. This includes alterations to the homepage, default search engine, or even the appearance of unfamiliar browser extensions. These changes are typically caused by adware programs that have hijacked the user’s browser and modified its settings to their advantage.
It is important for users to remain vigilant and take immediate action if they suspect their device has been infected with adware. Promptly addressing the issue can help prevent further disruptions and potential data breaches.
To detect adware infection, look out for the following signs:
- Sudden appearance of ads in unexpected places
- Browser settings changing without consent
Taking suitable and immediate action is crucial to prevent further disruptions and potential data breaches caused by adware infection.
The Rise Of Adware: Increased Volume And New Techniques
Adware is a persistent problem in the cybersecurity landscape, with its volume steadily increasing over the years. The proliferation of mobile devices and the integration of adware into mobile apps have contributed to this rise. Adware makers are also employing more aggressive techniques to evade detection and removal.
Adware developers have started hiding their malicious software within Trojans, thus increasing the chances of adware installation. Additionally, adware is often bundled with adfraud components, aiming to generate revenue through fraudulent practices.
Furthermore, some adware variants demonstrate capabilities similar to rootkits, allowing them to remain hidden and resist conventional removal techniques. These evolving tactics highlight the need for continuous improvement in cybersecurity measures to combat the increasing threat of adware.
Protecting Against Adware: Removal Techniques And Prevention Measures
To protect against adware, it is crucial to adopt proactive measures and follow best practices for cybersecurity. Regularly backing up files ensures that data can be recovered in case of an adware attack or any other cybersecurity incident.
In terms of adware removal, using the utility provided by the device’s operating system can be a good first step. However, some resilient adware may require specialized tools to completely eradicate them from the system. In such cases, downloading and installing reputable cybersecurity programs, like Malwarebytes, can help thoroughly scan and remove any traces of adware.
Prevention is always better than cure when it comes to adware. Users should exercise caution when downloading and installing new software, ensuring they read the terms and conditions carefully to avoid unwittingly installing adware. It is also important to avoid torrent sites and illegal downloads, as these are often breeding grounds for adware.
Furthermore, users should only download apps from trusted sources and should be wary of opening apps from unknown sources, as this can also lead to adware infections. Regularly scanning devices with reputable cybersecurity programs can provide an additional layer of protection against adware and other forms of malware.
Fresh insights added for marketers this week.
In conclusion, being aware of the existence and potential threats of adware is crucial in today’s digital landscape. By staying informed, exercising caution, and utilizing reliable cybersecurity tools, users can protect themselves from the nuisance and potential dangers associated with adware.
FAQ
1. How can users protect their devices from advertisement pop-up viruses?
Users can protect their devices from advertisement pop-up viruses by taking a few precautionary measures. Firstly, they should always keep their devices and operating systems up to date with the latest security patches. This helps to minimize vulnerabilities that could be exploited by viruses. Secondly, they should be cautious when downloading and installing apps or software from unfamiliar sources, as these can often contain hidden viruses. It is recommended to only download from trusted and verified app stores. Additionally, users should consider installing reputable ad-blockers or pop-up blockers on their web browsers to limit the chances of encountering advertisement pop-up viruses. Regularly scanning the device with antivirus software can also be an effective way to identify and remove any existing viruses.
2. What are the common signs and symptoms of an advertisement pop-up virus infecting your device?
The common signs and symptoms of an advertisement pop-up virus infecting your device include frequent and intrusive pop-up ads appearing on your screen. These ads may appear even when you’re not browsing the internet or using any specific app. They often redirect you to suspicious websites or prompt you to download fake or malicious software.
Additionally, you may experience a significant slowdown in your device’s performance, as the virus consumes system resources. Your device may also become more prone to crashes or freezes. It’s essential to address these signs promptly by running an antivirus scan and removing any detected malware to ensure the security of your device and personal information.
3. What are the potential risks and consequences of clicking on or interacting with advertisement pop-up viruses?
Clicking on or interacting with advertisement pop-up viruses can have several potential risks and consequences. Firstly, these viruses can often lead to the installation of malware or other harmful software on your device. Once installed, this malware can steal your personal information, such as passwords, credit card details, or personal documents, which can lead to identity theft or financial losses. Additionally, these viruses can also cause your device to slow down or crash, disrupting your productivity and potentially causing data loss. Overall, clicking on or interacting with advertisement pop-up viruses can pose serious security and privacy risks that can have significant consequences for the user.
4. How do advertisement pop-up viruses manage to bypass antivirus software and infect devices?
Advertisement pop-up viruses are designed to bypass antivirus software and infect devices by utilizing various tactics. One common method is by disguising themselves as legitimate advertisements or pop-ups, making it difficult for antivirus software to detect them as malicious. They may use advanced techniques like obfuscation or encryption to hide their code, making it harder for antivirus programs to recognize and block them.
Additionally, these viruses often exploit vulnerabilities or weaknesses in the operating system or web browsers, allowing them to sneak past antivirus defenses. They can take advantage of these vulnerabilities to install themselves on a device without being detected by antivirus software. Some pop-up viruses may also use advanced social engineering techniques to trick users into clicking on the ads, such as promising fake rewards or spreading fear or urgency.
Overall, advertisement pop-up viruses employ a combination of deceptive techniques, code obfuscation, and exploit vulnerabilities to bypass antivirus software and successfully infect devices.
Advertising Platform for Marketers • Self-Serve DSP Platform • Performance Marketing Tips • Programmatic Advertising